Digital Risk Protection (DRP)
Learn how to safeguard digital assets with digital risk protection.
Managed Digital Risk ProtectionWhat is Digital Risk Protection (DRP)?
Digital Risk Protection (DRP) is the process of safeguarding digital assets and brand reputation from external threats. As more business operations embrace digital practices, the threats and attack surfaces that can be exploited by threat actors increase. DRP solutions operate on the premise that organizations can use threat actor activity to their advantage to identify attacks before they happen.
Indeed, the Cybersecurity and Infrastructure Security Agency of the US Government (CISA) has said that information sharing amongst organizations operated within the private sector is critical in the quest for a more holistic understanding of the crosscutting and shared risks that may have cascading impacts within and across organizations, sectors, and national critical functions (NCFs).
This is why it’s imperative to institute a DRP solution that can correlate multiple sources of telemetry; one that can scan the clear, deep, and dark webs for potential dangers as well as proactively identify and research malware, phishing scams, and other threat actors.
It may seem overwhelming to be able to stand up a solution that can both connect these disparate sources of suspicious activity and also help defend a network. These days, however, there is no other choice but for security organizations to try and do just that – and then to push risk mitigation and threat intelligence strategies even further to continue to stay a step ahead of attackers.
How Does Digital Risk Protection Work?
DRP works by leveraging insights derived from Cyber Threat Intelligence (CTI) monitoring to highlight actionable and specific protections. CTI monitoring uses data from multiple sources to build a snapshot of the threat landscape. This can identify emerging threats against organizations and allow proactive mitigation before attacks occur.
DRP platforms use intelligent algorithms plus multiple reconnaissance methods to find, track, and analyze threats in real time. Using both indicators of compromise (IOCs) and indicators of attack (IOAs) intelligence, a DRP solution can analyze risks and warn security teams of potential or imminent attacks.
The data handling and analysis capabilities of DRP systems prevent security teams from being overwhelmed by intelligence data and therefore overlooking a relevant threat. They can continuously find, monitor, and mitigate risks that target an organization’s digital assets in real time.
A DRP system should also be able to simplify workflows through advanced investigation and mapping capabilities that can create highly contextualized alerts, freeing analysts from having to sift through noise. Businesses and security organizations are, after all, looking to drive forward underlying goals and broader initiatives; there is no way for an organization to pause its digital footprint from evolving.
Therefore, an effective DRP platform must also work to evolve alongside a security organization and business, identifying new potential attack vectors and anticipating the next area of exposure along a network and its systems.
The Four Quadrants of Digital Risk Protection
DRP requires a multifaceted approach. The four quadrants outlined below combine to deliver effective DRP solutions.
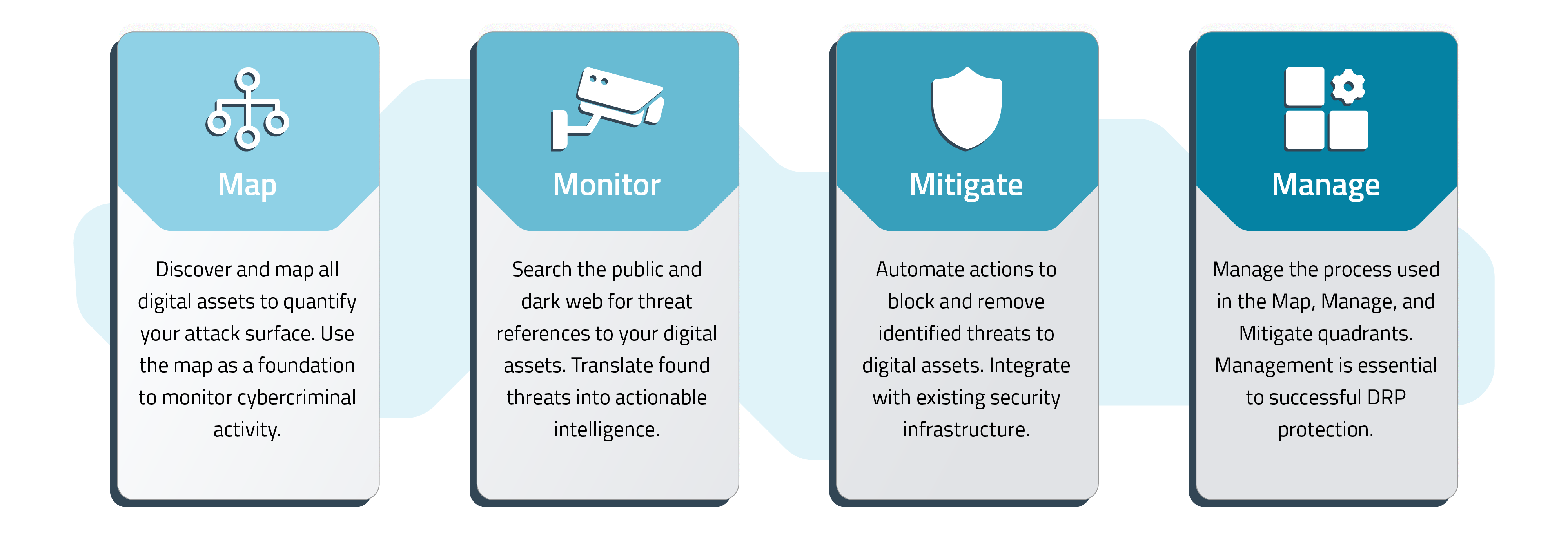
Map
Understanding the digital attack surface is essential to determine how and where threat actors might strike. This includes an assessment of digital assets and helps to create a foundation for how a security organization monitors suspicious threat activity.
Monitor
DRP solutions translate millions of data points into actionable business intelligence. This is accomplished with multidimensional threat analysis, digital footprint contextualization, and threat evolution tracking.
Mitigate
Automating the threat mitigation process with a DRP solution enables an organization to extend security support to other departments and company initiatives.
Manage
This refers to managing the DRP solution as well as implementing policies, additional threat research, human intelligence, enriching IOCs and prioritizing vulnerabilities.
Digital Risk Protection Use Cases
Effective DRP deployment can ease the security burden and enable teams to focus on essential business tasks. Let’s take a look at examples of how DRP built on comprehensive CTI can make life easier for IT professionals.
Phishing Detection
Phishing is the most common attack vector used by threat actors. Tracking phishing indicators – registered domains, mail exchange (MX) record changes, DNS reputation – with DRP can identify planned phishing scams and enable the takedown of impostor domains and sites.
VIP and Executive Protection
Spear phishing that targets real users within organizations is prevalent. DRP can identify spoofing plans and secure the digital assets belonging to VIPs, executives, and other personnel.
Vulnerability Prioritization
The volume of security data CTI and DRP collect and analyze is always increasing. DRP uses intelligent algorithms to automatically sift through this data and prioritize alerts for security teams. Focus is centered on the most imminent and pressing threat indicators.
Dark Web Monitoring
Most malicious cyberattack planning and activity occur on the dark web. DRP solutions monitor all places where criminal activity is discussed and planned, making the process vital to identifying and mitigating threats.
Brand Protection
Brands are valuable. DRP monitors for domain spoofing and IP address spoofing by using a brand or close analogues. Taking down these illicit activities protects a business' IT systems and its reputation.
Fraud Protection
DRP monitors for illegal financial and sensitive data auctions. Valuable data is sold on the dark web for use in phishing and other attacks, which means monitoring for this activity is crucial.
Malicious App Identification
Threat actors are acutely aware that mobile apps are essential to modern business, which is why they steal consumer data by deploying fake apps designed to mimic real apps. DRP can monitor for and highlight these malicious mobile apps.
Automated Threat Mitigation
Rapid response to identified threats is imperative. Automating responses based on predefined criteria delivers better security for both users and data.
Leaked Credentials Monitoring
Stolen login and other access credentials are valuable assets for threat actors. DRP solutions monitor the web for references to leaked credentials and alert security professionals upon discovery.
Sensitive Data Leakage Monitoring
Leaked data is also a valuable item for threat actors. DRP monitors for discussions about data breaches, and will alert when any references to an organization’s data are found on the web or dark web. This is particularly helpful in large data breaches containing complex data sets.
Supply Chain Risk Protection
Most organizations have extensive physical and digital supply chains. DRP can monitor for references to the systems used by suppliers so that there is less of a likelihood a breach occurs via a trusted-yet-unwitting supply partner with access to the business’ network.
Digital Risk Protection Services
By finding a security-service provider to help manage a DRP program, organizations can realize time-saving benefits that enable analysts to focus on larger issues affecting the business. But what should a security operations center (SOC) look for when searching for the right managed digital risk protection (MDRP) provider?
- Analysis: Manual and time-consuming processes can hinder the productivity of security personnel. Hours spent analyzing risk signals on the dark web or a web-based Git repository can easily be offloaded to an MDRP that brings expertise to tackle issues faster.
- Partnership: After spending hours/days/weeks in the trenches, an MDRP provider should be able to come back with clear and actionable insights to share with a client and collaborate on a plan to move forward.
- ROI: If an organization has landed on the right partner for their specific needs, ROI should likely follow in time. A regular retainer will, of course, go to the MDRP provider, but as efficiencies are created the service will likely pay for itself and then some.
- Risk comprehension: Security organizations will gain rapid and unprecedented visibility into their risk profiles and the benefits this can impart to the overall business, particularly as a provider helps mitigate threats like data leakage, stolen executive credentials, and securing brand reputation in the face of a threat.
- Business outcomes: Lastly, by assuming the weight of risk analysis and protection, an MDRP provider will be able to help their clients take a more proactive stance when it comes to risk mitigation. It isn’t enough to react in this modern threat environment; organizations must be proactive in increasingly intelligent ways.
Read More About Digital Risk Protection
4 Simple Steps for an Effective Threat Intelligence Program
Evolution of Cyber Threat Intelligence (CTI)
Threat Intelligence News: Latest Rapid7 Blog Posts